The Facts About Parental Control Software Revealed
Wiki Article
Internet Safety Can Be Fun For Everyone
Table of ContentsThe 7-Minute Rule for Online Identity ProtectionThe Only Guide to Online Identity ProtectionSee This Report about Internet SafetyA Biased View of Parental Control SoftwareFascination About Vpn ServicesSome Ideas on Vpn Services You Should Know
If we speak about it specifically it's Part 2 of Avoidance of Electronic Crimes Act, 2016, that supplies info regarding criminal offenses of computer abuse and to bill for the certain criminal offense. Stealing and abuse of individual data. As computer has many means where people can steal data and also misuse it, as computer is a tool which is fast as well as procedure any kind of job rapidly, so when it comes to the moving or copying information it makes with ease as well as in seconds.
If some prohibited or uncertified gain access to that has been used for hacking objective, where an uncertified person makes use of a computer system, network or the Internet to hack the target's system without having any type of sort of authorization to get and also control the system. Whenever the system is hacked the sufferer don't recognize anything that his/her data has actually been hacked as well as the majority of the time hackers do hacking to risk the target.
That the computer system or any kind of system will not be hacked conveniently as their safety and security of accessing system will certainly be high. When a crime is done by a specific then he or she is obliged for certain criminal offense then that person is charged with high quantity of money as the fees for underhanded misuse of somebody privacy, and sometimes, there are imprisonment if the bad guy was included in numerous criminal activities.
Internet Safety - The Facts
So, the adult youngster can easily accessibility. These obscene products have high danger damages the future of young generation, yet the law states it is a criminal offense to generate as well as disperse off-color product that is not good for the youth that are listed below age of 18. Primarily, the act of severe criminal offenses will be made use of to offer the penalty to the individual that makes use of computer modern technology and also the Net to get, spread out or share/distribute the vulgar material that include vulgar videos, photos.These companies have actually supplied center to report them on-line and also via their specific get in touch with to ensure that the individual can report regarding the kid sex-related misuse notify of pictures or videos in an extremely protective way so the wrongdoer can be detained as well as from the Web to remove and also wipe these kinds of profane things or material.

Things about Vpn Services
That creates substantial cash loss to the person. All of us recognize that social websites and also apps are the resources via which individuals connect and also share their individual life celebrations with buddies, yet as a result of these instances connected to on-line harassment is boosting on a daily basis, where an individual makes use of Net solutions to maintain an eye on the target while remaining confidential and also making use of public teams or internet sites to get information about their victim.
That cause not only loss of money, however the customers' trust. To stop from these kind of attacks banks should take safety and security safety measures and protected process for the online transactions, to stay risk-free in future from this kind of incident. There are numerous legislations which supplies defense to every customer of the Web from bad guys who utilizes network to damage the customers, yet the federal government must take some actions to make entities that advise the organizations that apply the legislation, that exactly how to inquiry those criminal activities which belongs to the Net as well as offer in efficient method.
Not known Details About Parental Control Software
It is essential for every Web user to take the value about the safety and security and also regulations generally which handles the criminal offenses that are triggered by the improper use computer system. And also there must be an appropriate way for get more the safety monitoring to protect and secure the systems, as well as the particular data inside them.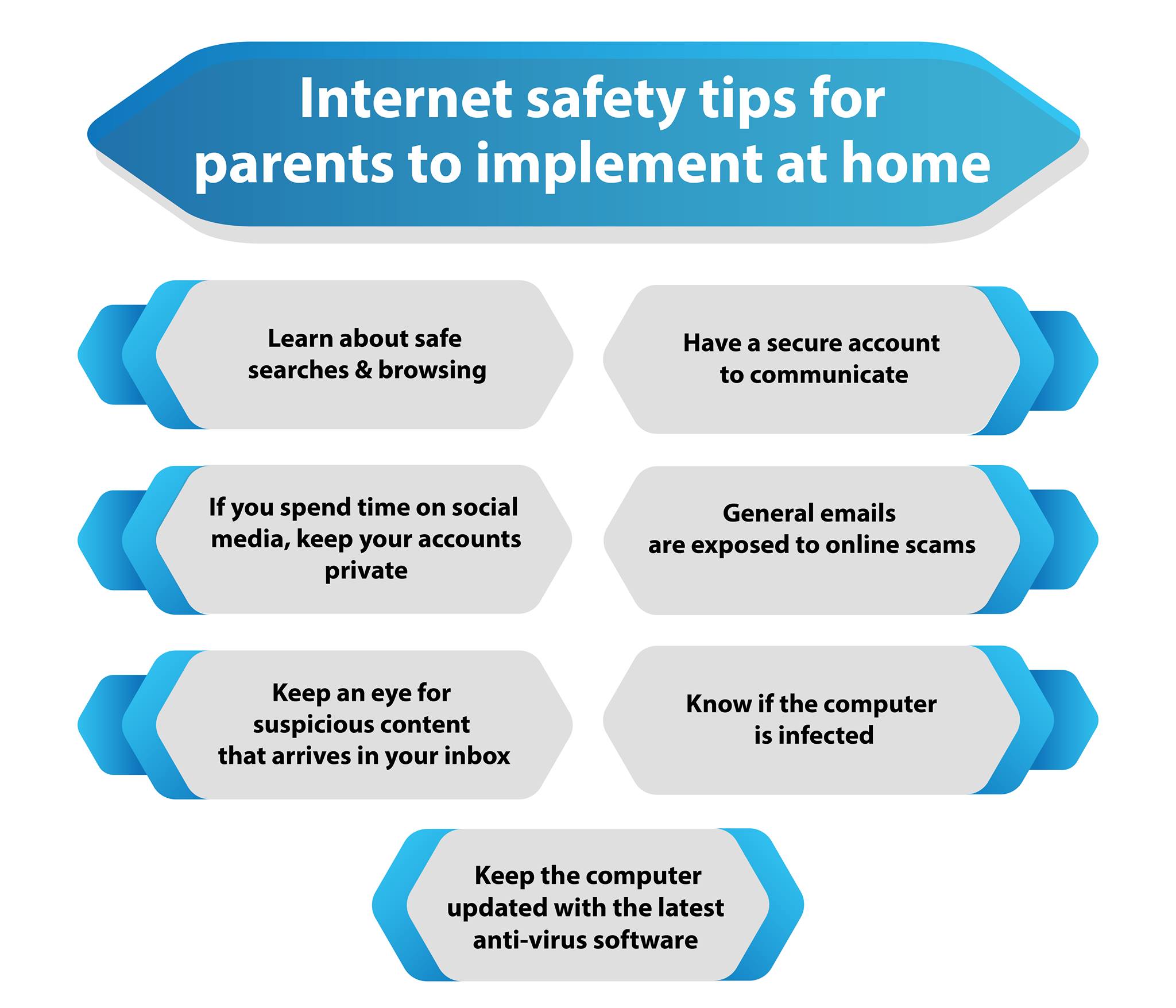
The value of cybersecurity in the electronic world is immense. It is because the quantity as well as sophistication of cyberattacks are regularly raising. As our reliance on technology expands, so does our susceptability to these strikes. Cybersecurity aids to secure our data and systems from these threats. The significance of cyber safety in the digital globe can not be downplayed.
Some Known Details About Online Identity Protection
Cyber safety and security is essential for students since they commonly target online attacks. In a current situation, a team of trainees from a college in the USA was targeted by hackers that accessed to their personal information, including their Social Security numbers and also credit card details. The hackers then utilized this info to fraudulently charge countless bucks to the students' bank card.This instance highlights the value of cyber safety and security for pupils, that are frequently the sufferers of cybercrime. If a student's individual details is stolen in a cyber assault, it might be used to commit identity theft. It might mess up the pupil's credit history, making it hard for the pupil to get finances for university or a vehicle.
The significance of Cyber Safety for organizations and also organizations can be seen when it comes to the target data breach. In this instance, cyberpunks were able to access to the target's consumer information, consisting of debt as well as debit card details. It resulted in target needing to pay out millions of bucks in problems and also shedding client trust fund.
The Basic Principles Of Cybersecurity Training
An additional information violation example would be the Wan na, Cry ransomware attack, which targeted services as well as organizations worldwide. This attack resulted in the loss of data and money for many companies, as well as some were also required to close down (VPN services). certified Ethical Hacking courses for individuals to function towards protecting information from violations and also malware.If this information had dropped right into Website the wrong hands, it can have been made use of for identification theft, fraudulence, or various other harmful purposes. In the last few years, there have been a number of prominent cyberattacks that have had a destructive influence on organizations and people. Cybersecurity training. These are theft of social security numbers, savings account information, credit score card information, and also delicate information leaks
Report this wiki page